All-In-One Content Discovery Scanner
Discover Hidden Web Content & Security Vulnerabilities.
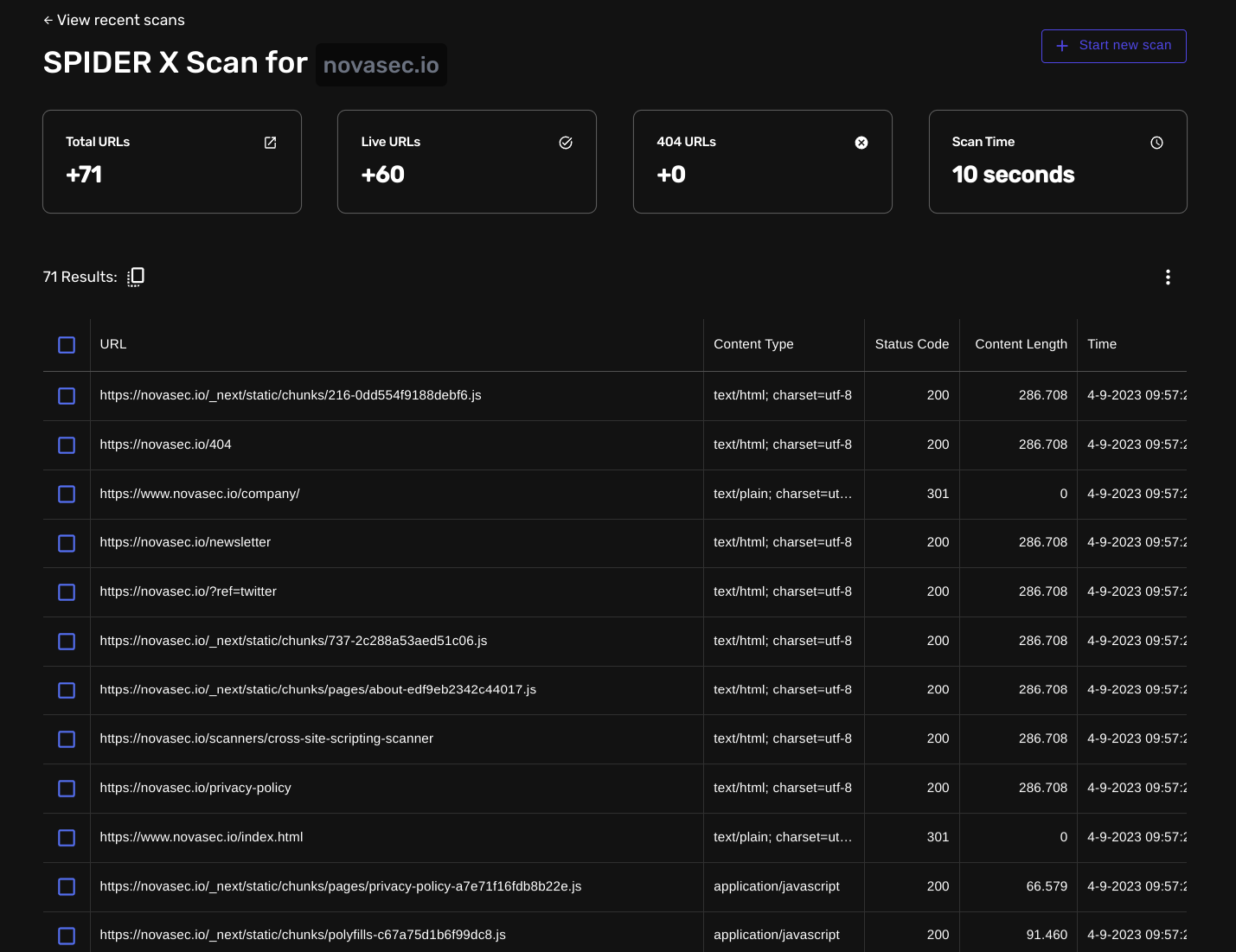
Discover More Hidden Directories
Here's what makes SPIDER X unique:
Simulate Penetration Tester's Behaviour
SPIDER X mimics a pentester's behaviour as it crawls and intercepts all pages using a headless crawler and a valid User-Agent.
Find More Content
With the built-in headless crawler capabilities & the targeted bruteforcing, you'll be able to find much more files, app routes, API endpoints, and JavaScript files!
Built-in URL Filter
Easily get rid of useless 404 pages with our built-in option to filter for URLs.
Versatile
SPIDER X fully integrates with our platform! You can easily select and send multiple URLs to get them scanned for other security vulnerabilities!
Detailed Overview
An easy & detailed overview, with numerous filters to easily find patterns for what you're looking for: vulnerabilities.
Export Results
Export your results with a single click and process URLs however you like.
FAQ
Frequently asked questions
Is SPIDER X a headless web crawler?
Is SPIDER X a headless web crawler?
Yes, that's what makes it powerful over other tools that are currently in the market. It is able to stealthily mimic normal user behaviour and with that intercept every single request sent from and to the client (web browser). This in turn allows it to pickup javascript files that are dynamically included as well for example, an approach that most modern web frameworks use to minimize load times and increase performance.
Does SPIDER X perform bruteforcing?
Does SPIDER X perform bruteforcing?
Yes, SPIDER X performs targeted bruteforcing based on the technologies identified on the supplied target or asset.
Is SPIDER X capable of performing JavaScript file enumeration?
Is SPIDER X capable of performing JavaScript file enumeration?
Yes, as afterall, the most interesting app routes and endpoints are mostly referenced in JavaScript files.
Is SPIDER X capable of crawling for links behind authenticated parts of my website?
Is SPIDER X capable of crawling for links behind authenticated parts of my website?
Yes, you can easily supply request headers (including any authentication headers) to reach parts behind a login form.
Is SPIDER X capable of enumerating parameters?
Is SPIDER X capable of enumerating parameters?
Yes, SPIDER X is capable of enumerating potential query parameters in requests (URL, request & response bodies), JS Files. SPIDER X is also capable of intercepting parameters that are processed on the client-side (and will mark them as such as they are more likely to be vulnerable to DOM-based vulnerabilities).